5 minutes reading time
#前言
在7月份 go 团队正式推出了官方的漏洞检测工具 - govulncheck, govulncheck 默认向 https://vuln.go.dev/ 漏洞数据库请求, 对数据库的请求不包含代码只有使用的包,你也可以使用 -db 来指导所使用的漏洞数据库,所使用的数据库必须实现相应的规范。
govulncheck 具有以下限制:
- Govulncheck在分析函数指针和接口调用时采用保守的方法,这可能导致一些情况下的误报或不准确的调用堆栈。
- 使用reflect进行的函数调用对于静态分析是不可见的。仅通过这些调用才能访问的易受攻击的代码将不会被报告。使用unsafe包可能导致漏报。
- 由于Go二进制文件不包含详细的调用信息,govulncheck无法显示检测到的漏洞的调用图。对于二进制文件中但无法访问的代码,它可能还会报告误报。
- 目前还不支持 silencing 漏洞发现。请参阅https://go.dev/issue/61211 。
- Govulncheck只能读取使用Go 1.18及更高版本编译的二进制文件。
- 对于无法提取符号信息的二进制文件,govulncheck会报告二进制文件所依赖的所有模块的漏洞。
govulncheck 架构图
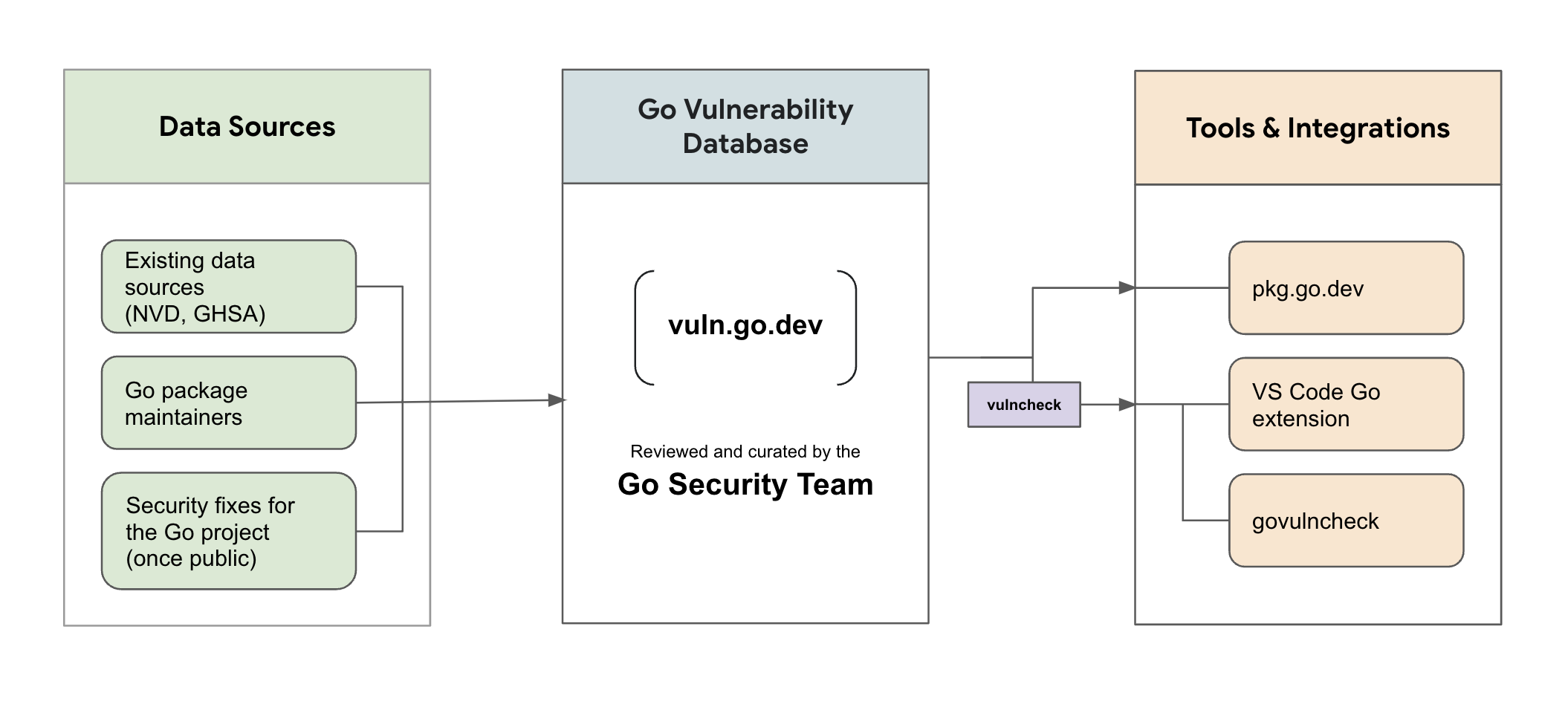
govulncheck 还提供了一个可用的 API govulncheck,使开发者能够方便的将 govulncheck 集成到各种工具之中。
#安装
通过以下命令安装 govulncheck:
go install golang.org/x/vuln/cmd/govulncheck@latest
#使用
安装完 govulncheck 后,我们就可以使用了,进入项目路径中,执行 govulncheck ./... 。
以下是我的一个项目的输出:
Scanning your code and 508 packages across 71 dependent modules for known vulnerabilities...
Vulnerability #1: GO-2023-2102
HTTP/2 rapid reset can cause excessive work in net/http
More info: https://pkg.go.dev/vuln/GO-2023-2102
Standard library
Found in: net/[email protected]
Fixed in: net/[email protected]
Example traces found:
#1: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls http.Server.Serve
#2: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls http.Server.ServeTLS
Vulnerability #2: GO-2023-2043
Improper handling of special tags within script contexts in html/template
More info: https://pkg.go.dev/vuln/GO-2023-2043
Standard library
Found in: html/[email protected]
Fixed in: html/[email protected]
Example traces found:
#1: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls template.Template.Execute
#2: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls template.Template.ExecuteTemplate
Vulnerability #3: GO-2023-2041
Improper handling of HTML-like comments in script contexts in html/template
More info: https://pkg.go.dev/vuln/GO-2023-2041
Standard library
Found in: html/[email protected]
Fixed in: html/[email protected]
Example traces found:
#1: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls template.Template.Execute
#2: cmd\xxx\main.go:94:19: xxx.main calls kratos.App.Run, which eventually calls template.Template.ExecuteTemplate
=== Informational ===
Found 3 vulnerabilities in packages that you import, but there are no call
stacks leading to the use of these vulnerabilities. You may not need to
take any action. See https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck
for details.
Vulnerability #1: GO-2023-2045
Memory exhaustion in QUIC connection handling in crypto/tls
More info: https://pkg.go.dev/vuln/GO-2023-2045
Standard library
Found in: crypto/[email protected]
Fixed in: crypto/[email protected]
Vulnerability #2: GO-2023-2044
Panic when processing post-handshake message on QUIC connections in
crypto/tls
More info: https://pkg.go.dev/vuln/GO-2023-2044
Standard library
Found in: crypto/[email protected]
Fixed in: crypto/[email protected]
Vulnerability #3: GO-2023-1988
Improper rendering of text nodes in golang.org/x/net/html
More info: https://pkg.go.dev/vuln/GO-2023-1988
Module: golang.org/x/net
Found in: golang.org/x/[email protected]
Fixed in: golang.org/x/[email protected]
Your code is affected by 3 vulnerabilities from the Go standard library.
Share feedback at https://go.dev/s/govulncheck-feedback.
输出内容分为2块,第一块是 Vulnerability 信息,是项目中存在的漏洞,可以看到发现了3个漏洞及具体的原因、触发函数、发现的版本和修复的版本。第二块是 Informational 是一些没有直接引用的包中存在的安全漏洞。
根据漏洞所在的宿主不同,第一部分的信息也可以分为两类:一类是Go语言自身(包括Go编译器、Go运行时和Go标准库等)引入的漏洞,另外一类则是第三方包(包括直接依赖的以及间接依赖的)引入的漏洞。
针对这两类漏洞,我们的解决方法有所不同。
第一类漏洞的解决方法十分简单,直接升级Go版本即可,比如这里我将我的Go版本从Go 1.18升级到最新的Go 1.18.6即可消除上面的所有第一类漏洞。 对于第三方包这种情况,如果是直接使用的,可以直接升级到相应版本,如果是间接引用的我们要根据直接引用的包的修复情况来决定。
#小结
本文介绍了 go 官方团队新推出的安全漏洞检查工具 govulncheck,通过使用这个工具我们能够轻松的检查出 go 代码中存在的漏洞。
#参考
- https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck
- https://go.dev/blog/govulncheck
- https://go.dev/blog/vuln
- https://go.dev/security/best-practices
- https://github.com/golang/go/issues/61211
- https://go.dev/security/vuln/editor
- https://go.dev/doc/tutorial/govulncheck
- https://pkg.go.dev/golang.org/x/vuln/scan